
d-CON® Mouse Prufe® II - Wedge (Discontinued)
Price: $ 7.00
5(144)

Analyzing attacks taking advantage of the Exchange Server vu - vulnerability database

Donkey anti-Mouse IgG (H+L), Alexa Fluor™ 594 (R37115)

D-CON Pesticide at
fragilepulse/words.json at master · kbooten/fragilepulse · GitHub

Mice & Computers Surplus
You don't have to come in contact with mice to eliminate them from your home. When you're looking for a simple, mess-free solution to rodent problems,

D-CON

D-Con Mouse Prufe Ii, Pest Control

Microsoft Exchange 2019 SSRF / Arbitrary File Write - exploit database

Unimouse (2.4Ghz Wireless Technology, 6 programmable Buttons, 10 DPI Settings, Pixart PMW3330 Sensor) (Left-Hand Wireless) : Video Games

HAFNIUM targeting Exchange Servers with 0-day exploits - vulnerability database

Analyzing attacks taking advantage of the Exchange Server vu - vulnerability database
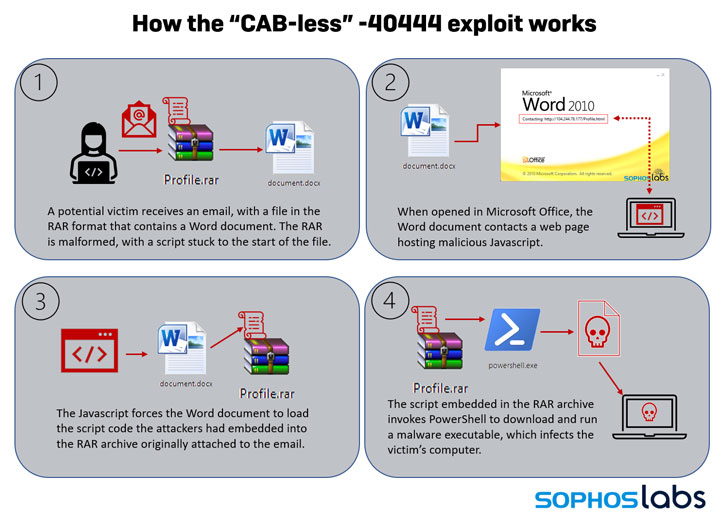
New Exploit Lets Malware Attackers Bypass Patch for Critical - vulnerability database




